Hi @anthonysena ,
I see the sign in button and I am able to log in using my Windows credentials.
Here is my SEC_USER table:
ID, LOGIN, PASSWORD, SALT, NAME
1003, WINDOWS\USER, NULL, NULL, NULL
And my SEC_USER_ROLE table:
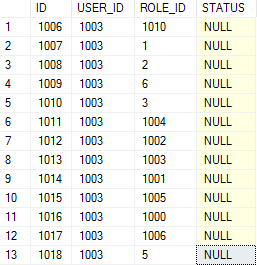
ROLE_ID from 1000 to 1006 correspond to ‘Source user’